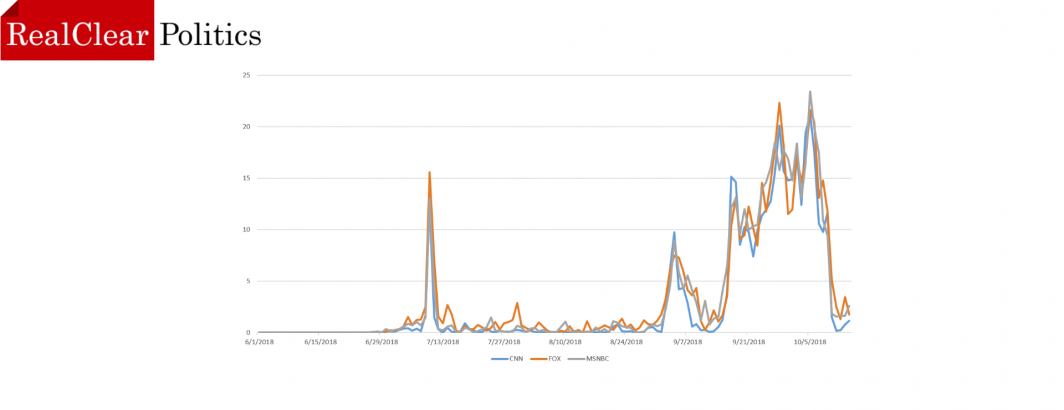
RealClearPolitics: The Kavanaugh Confirmation Through The Eyes Of Television
A look back at how the major networks covered the Kavanaugh confirmation hearings, yielding some surprising findings about what constitutes…
Welcome To The New GDELT Blog
We're excited today to announce the debut of our our new blog, our first major redesign in four years! Our…
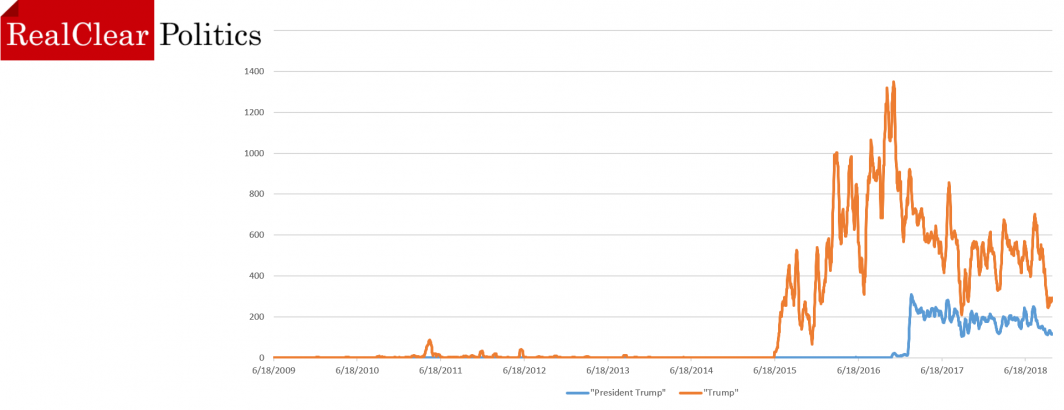
RealClearPolitics: The Game Of The Name: Media Bias And Presidents
More than a year and a half into the new presidency, CNN and MSNBC still refer to Barack Obama as…
Cloud Inference API Scoring Guide
Google's Cloud Inference API documentation uses GDELT to demonstrate how scoring works. Read The Full Article.
What Facebook's Russian Data Leak Shows About Government Surveillance And Facial Recognition
Facebook has become a critical surveillance tool for governments, from tracking dissidents to building facial recognition systems, reinforced by its…
Why Facebook's Breach Should Mean #DeleteFacebook But Won't
The sad truth is that Facebook's network has become so ingrained in society across the world that we simply cannot…
Google's BigQuery Brings GIS Into The Petascale Era
BigQuery’s unique ability to couple petascale query infrastructure with thousands or even tens of thousands of cores and apply it…
Why Instagram's New Anti-Bullying Filtering Is So Dangerous
From their early roots as absolute defenders of free speech, social media platforms have embraced black box filtering without any…
Viewing Social Stratum Differences and Logic from Big Data – Analysis Based on Internet Big Data GDELT
This Chinese-language analysis examines how GDELT can be used to understand Chinese society using GDELT. The Google Translate machine translation…
No Google Isn't Trying To Censor The Web
Google's presentation captures a company not presenting a vision for global internet censorship, but rather a company asking the most…
Will Governments Turn Our Smart Devices Into A Massive Surveillance Network?
The biggest privacy threat from smart devices is not companies mining our data, but rather governments waking up to their…
Can We Finally Stop Terrorists From Exploiting Social Media?
Hash-based blacklisting has become the dominate approach to fighting terrorism online, but fails to understand context. We have the tools…
Let's Encrypt And The Free Future Of HTTPS
As major web hosting companies embrace free automatic SSL services like Let’s Encrypt, securing the web should be easier than…
Facebook's Portal Camera And The Growing Privacy Concerns Of Bringing Cameras Into Our Homes
We are increasingly inviting Orwellian surveillance devices into our homes, filling our most intimate spaces with internet-connected cameras and microphones…
Is Social Media Empowering Or Silencing Our Voices?
The social media platforms that once empowered the world’s citizenry have instead today silenced those voices, elevated the elites and…
Do We Need To Teach Ethics And Empathy To Data Scientists?
Standing between a safe and privacy-first web and an Orwellian online dystopia is the empathy and ethics of those creating…
Should Social Media Be Responsible For Illegal Ads On Their Platforms?
The pinpoint targeting of social media ads allows for for one-click discrimination, but what responsibility do the platforms have for…
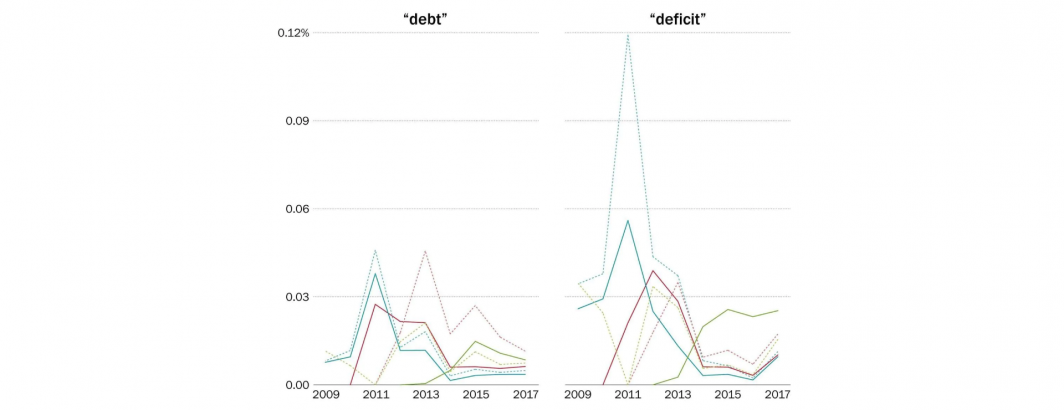
WashPost: Go For It, Brian Kilmeade
The Washington Post's Erik Wemple used the Television Explorer to explore trends in how the major networks have covered the…
A Globalized Cloud For A Globalized World
The modern public cloud is increasingly abstracting away the impact of geography, allowing companies to deploy globalized applications without changing…
The Chinese 'Spy Chip' Story Is A Reminder Of How Insecure Our Digital World Really Is
Bloomberg's story of the Chinese government covertly installing 'spy chips' on computers used in major commercial and US Government data…
What Facebook's Address Book Mining Tells Us About Our Privacy
Facebook’s silent practice of mining uploaded address books for contact information on other users reminds us that little has changed…
Will Twitter's New Democratic Policymaking Succeed?
Twitter announces it will involve its users in setting policy, but its inaugural attempt falls short. Instead, we need transparency…
Why Facebook's Breach Shouldn't Turn Us Away From Single Sign On
Facebook's breach raises questions about Single Sign On systems, but if the web embraced Estonia's model of hardware cryptographic identities…
What Facebook's Breach Teaches Us About How It Views Security
Most remarkable about the Facebook story is not that a breach happened, but rather that the company took so long…